Windows 11 is here already with a completely refurbished interface, several new security features, including some for Business and Enterprise – and some productive functionality and multitasking improvements too! Windows 11 is available as a free download and if you haven’t yet upgraded your PC, you should.
Windows 11 Tips and Tricks
Since the new operating system is here and most of us have downloaded it, here we are with some simple and some not so simple Windows 11 tips and tricks to improve your computing & browsing experience and increase your productivity.
- Pin apps to the Start Menu
- Dictation with punctuation
- Sound Settings
- Snap layouts
- Taskbar on all your displays
- Adjust taskbar alignment
- Reset network settings
- Turn off notifications
- Remove unwanted personalized ads on apps
- Block pop-ups and tracking in MS Edge
- New options in right-click
- Widgets
- Touch keyboard
- Change the default location
- Search settings.
If you are a beginner, you may want to go through our Windows 11 Tutorial first.
1] Pin/Unpin apps to the Start Menu
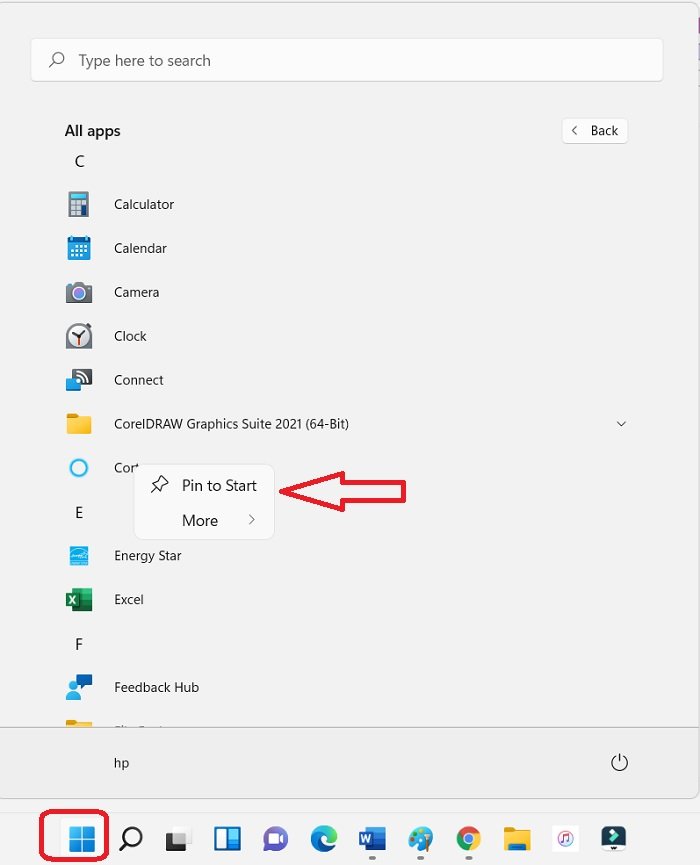
There is a new Windows 11 logo in your taskbar, that’s your new Start Menu which includes the pinned apps directly on the main menu. Launch the Start menu. Click on All Apps and it will display the list of apps available on your PC, right-click on the app you want to pin and click on Pin to Start.
Similarly when you want to unpin an app from the Start menu, right-click on that particular app and click on Unpin from Start.
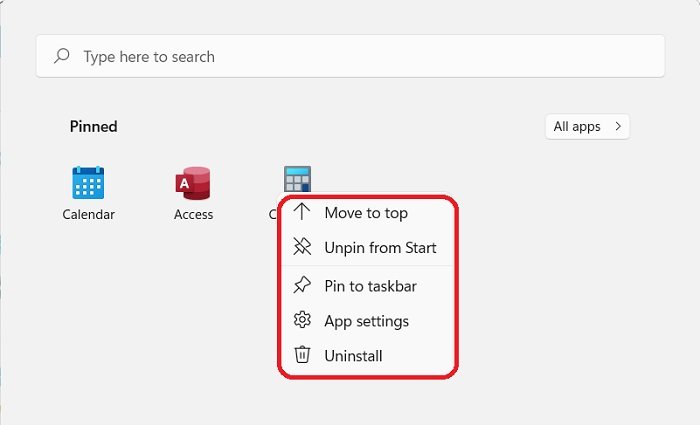
From here you can also adjust a few more settings like moving any app to the top, Pin to taskbar, Uninstall the app or Check the settings.
Read: How to customize your Windows 11 Start Menu.
2] Dictation with punctuation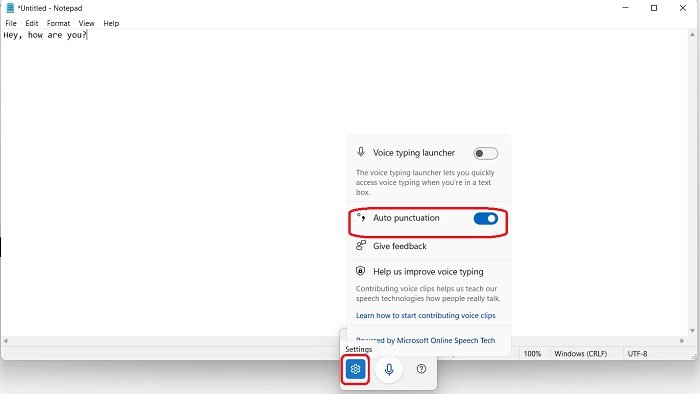
The Narrator in Windows 11 has got a new feature of auto-punctuation. Yes, it means the dictation you will give will automatically add the punctuations where required.
Open Notepad and press Win+H keys on your PC. It will open the Dictation. Click on the Settings icon and toggle the tab, “Auto punctuation’. The dictation will now automatically add the punctuations when and where required.
Read: How to use the new Windows 11 Explorer.
3] Sound Settings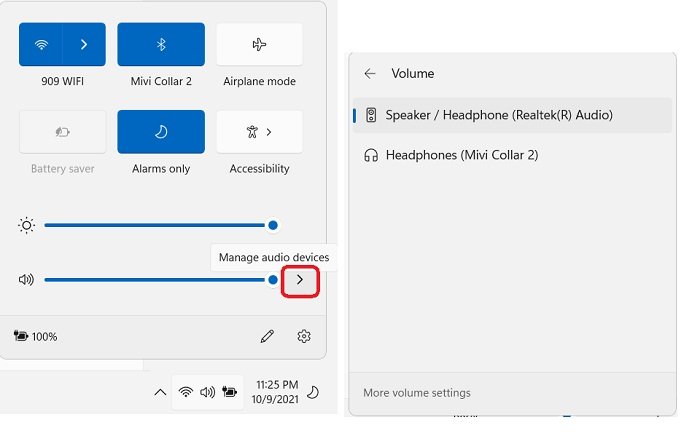
With Windows 11, you can now adjust the sound settings right from your System Tray. Actually, Network settings, Sound Controls, and Battery Settings are now combined in one button. Click on any of the icons in the System Tray and it will open all the settings.
To adjust the Sound Controls, click on the arrow next to the volume button and it will show you all the audio devices connected to your PC for output, you can switch between them easily with a single click. 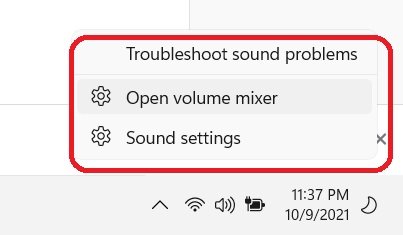
Not just this. You can now control the Volume Mixer too right from your desktop now. Right-click on the volume icon and you can see the direct link to Volume Mixer and other Sound Settings on your PC.
Read: How to get the old Right-click Context Menu back on Windows 11.
4] Snap Layouts
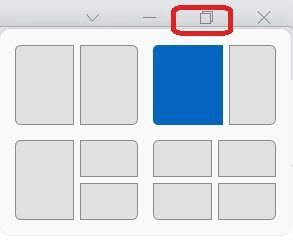
Microsoft has added a new feature named Snap Layouts in Windows 11. In Windows 10, when we used to open a window, we normally had only three options, to minimize, maximize or close the window, but now, you can see six different snap layouts. Pick any.
Read: How to Add Folders to Windows 11 Start Menu.
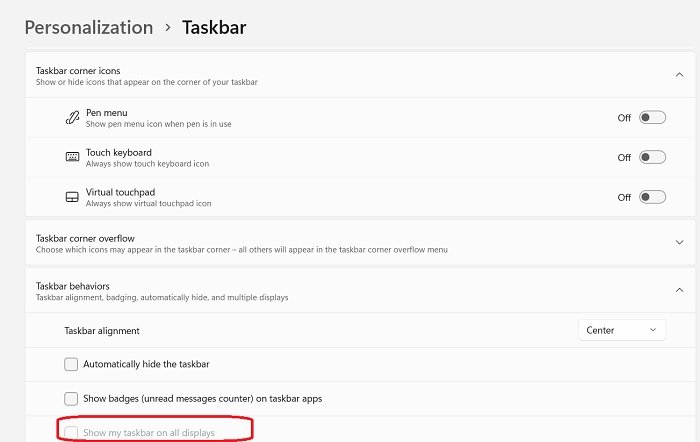
5] Show the taskbar in all your displays
With the new operating system, you can now view the taskbar in all your displays. By the way, the taskbar also has a whole new look now. To view the taskbar in all your displays-
- Right-click on your desktop and go to Personalize
- Scroll down to Taskbar
- Scroll down to Taskbar Behaviours and you will see the option ‘Show my taskbar on all displays”
- And you are done.
Read: How to reset Taskbar Corner Overflow Icons in Windows 11.
6] Move Start Menu to the left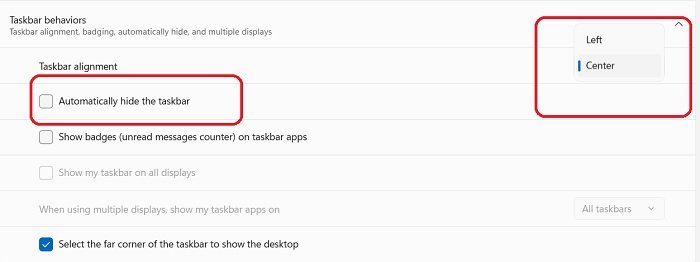
The Start Menu is not in the center and it looks great but yes you can align it to the extreme left if you want. To move your Start button and menu to the left-
- Right-click on your desktop and click on Personalize. (Alternatively, you can right-click on the taskbar and open the Taskbar settings directly)
- Scroll down to the Taskbar
- Under the tab Taskbar Behaviours, you will see the Taskbar alignment option.
- Select Left and your Taskbar will shift to the extreme left of your screen.
- You can bring it back to the center whenever you want to.
- There is also an option to hide the taskbar here as shown in the screenshot above.
You can also set up a Vertical Taskbar in Windows 11.
Read: How to customize Windows 11 Taskbar area.
7] Reset Network Settings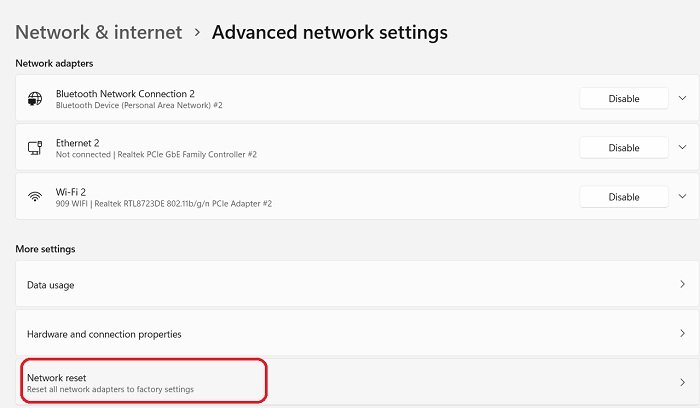
Microsoft has added an option in the Settings to help you if you are facing any difficulties in your network connectivity. This error often comes when your drivers are not up to date or some settings are not configured correctly.
- Launch Start, go to Settings.
- Choose Network and Internet.
- Go down to Advanced Network Settings and click on Network Reset.
- This will reset all your Network Adapters to the factory settings.
Doing this will remove and then reinstall all your network adapters and will also set the other network components back to their original settings.
Read: How to customize Windows 11 Quick Settings.
8] Turn Off Notifications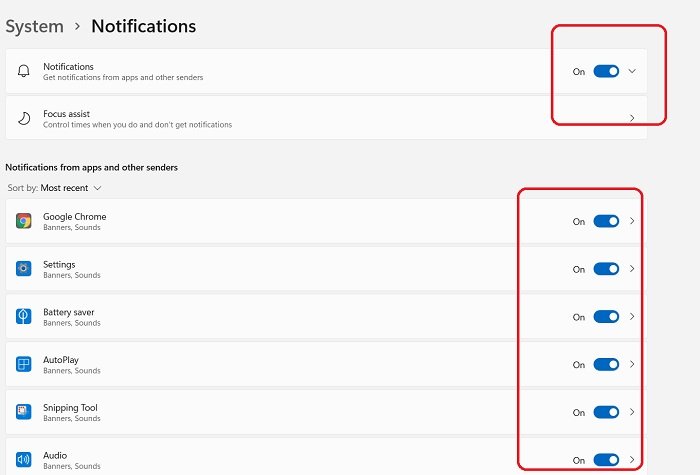
With Windows 11, the number of notifications has actually increased and this might be annoying to some. Well, thankfully we can turn the notifications off.
- Go to Settings from the Start Menu, alternatively, you can also press Win+I to open the Settings directly.
- Go to System and then click on Notifications.
- The Notifications are kept On by default but you can easily turn it Off if you want to.
- You can also adjust the notification settings for all the apps on your PC separately.
Read: How to customize the Windows 11 Lock Screen.
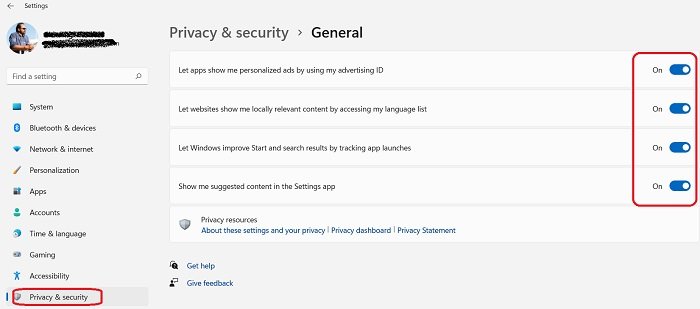
9] Remove Unwanted Personalized Ads on Apps
With the updated operating system, you now have better control over your privacy. With just a single click you can stop the apps using your data to show you the personalized ads.
- Go to Settings, and then go to Privacy & Security.
- From the right panel click on General Settings.
- Here you can select if you want the apps and websites to show you the relevant ads and content based on your interests and languages.
Read: How to block Ads in Windows 11.
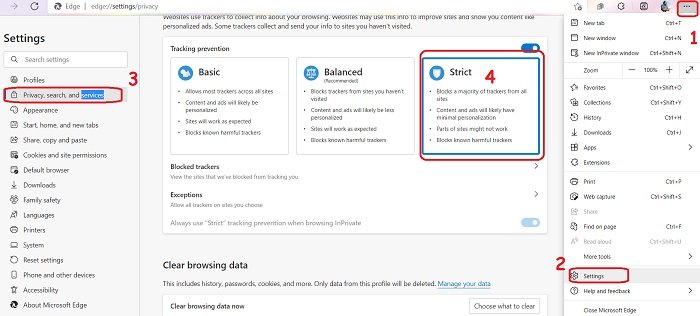
10] Block Pop-Ups and Tracking in Microsoft Edge
Now you might want to check these couple of settings in Microsoft Edge too.
- Launch Microsoft Edge on your PC and go to the Settings by clicking on the three dots on the top right corner of your browser.
- From the left panel, click on Privacy, Search, and Services.
- In the left panel, you will see that by default it is set to Balanced, but we would suggest you select the Strict option.
- This will block the majority of trackers, blocks the known harmful trackers and content will contain minimum personalization.
Read: How to Hide Badges on Taskbar Icons in Windows 11.
11] New options in Right-Click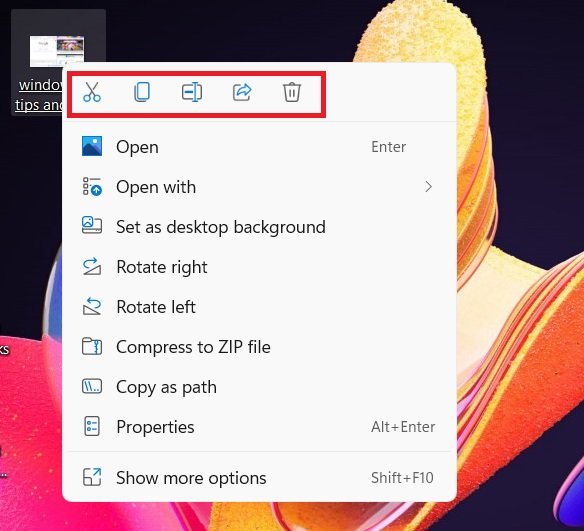
You might not have noticed but there are some changes in the right-click options in the new Windows 11. Now when you right-click on any file on your PC, you will see many new options added. The older cut, copy, delete, etc are now moved as icons.
Read: How to install the hidden Aero Lite theme in Windows 11.
12] Widgets
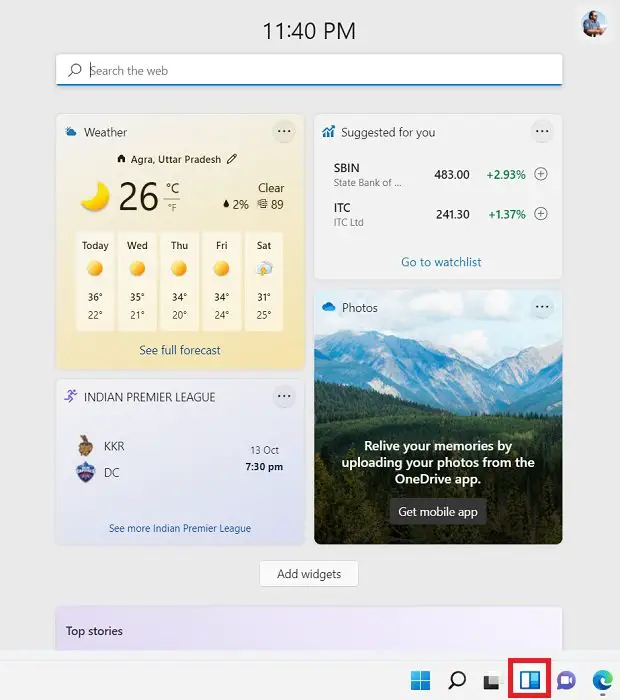
This is one of the many new features added to Windows 11. This is actually the new name and refurbished look of News and Interest that we had in Windows 10. The News and Interests icon earlier was placed in the System Tray in the bottom right corner of our screens. You can add or customize the widgets here as per your interests.
Related: How to remove or disable Widgets on Windows 11 Taskbar.
13] Touch Keyboard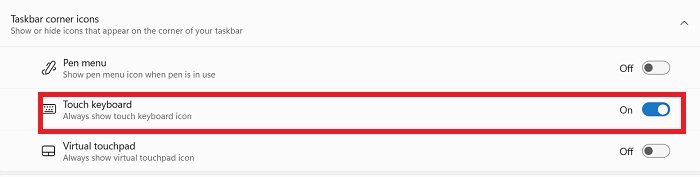
If you have a touch-enabled Windows 11 device, Windows 11 has the touch keyboard for you. Right-click on the taskbar to open the taskbar settings. Under the tab, taskbar corner icons, you will see the Touch Keyboard button. 
Turn it On to always show the touch keyboard icon in your taskbar. You will now have a small touch keyboard icon in always your System Tray, right beside the WiFi icon.
Windows 11 now also allows you to change the Touch Keyboard theme!
Read: Windows 11 Keyboard shortcuts you should know.
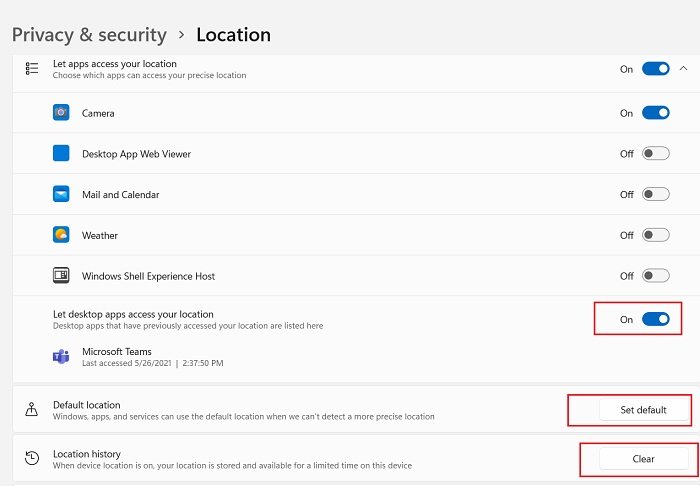
14] Change the default geolocation of your PC
We know that almost every app installed on our PC has access to our location. You can change your default location if you want to. You can also decide if at all you want the desktop apps to access your location or not. 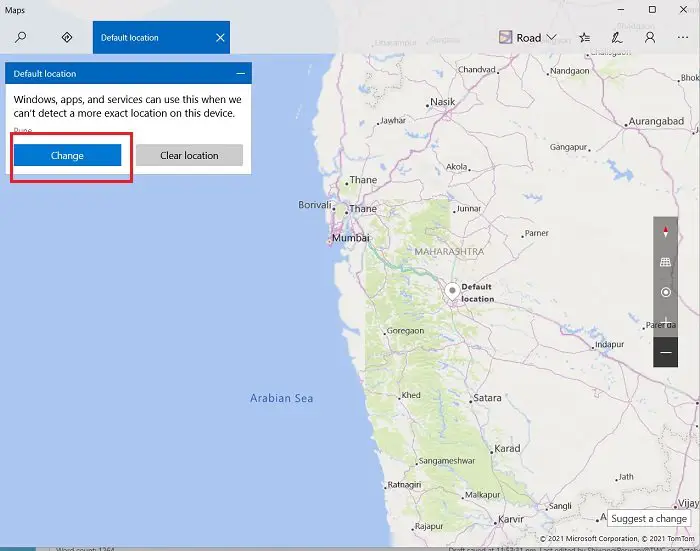
- Press Win+I to open Settings.
- Go to Privacy & Security.
- Scroll down and click on the tab Location.
- If you want to change your default location, click on Set default and it will open the Maps for you.
- Enter your location and click on Change.
Read: How to decrease the space between the items in Windows 11 Explorer.
15] Tweak Search Settings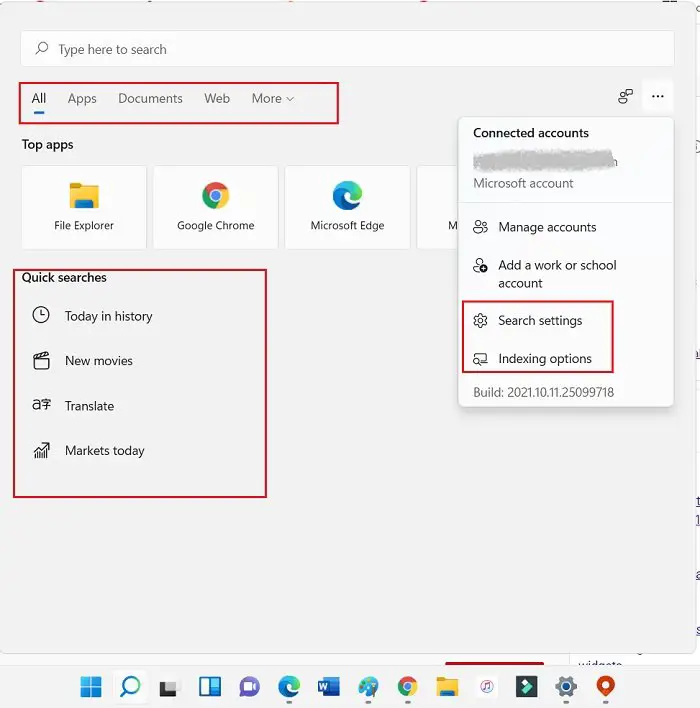
The Search pane in the taskbar also has its all-new look and features. Anything that you type in the Search bar will be searched for in the Apps, Documents, web, and more. The apps you use frequently are placed right on the Search pane. All your frequent searches are actually indexed here.
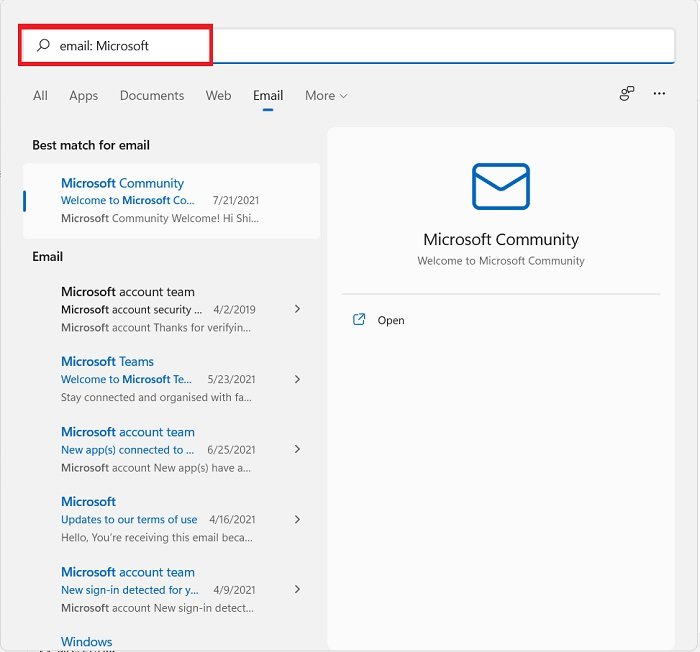
You can also be specific about where you want to search. For example, if you want to search for something in your email, click on the More tab and select email. Now type in what you want to search in your emails. So basically, you don’t really need to go to your email account to search for an email, you can do that directly from the Windows Search option.
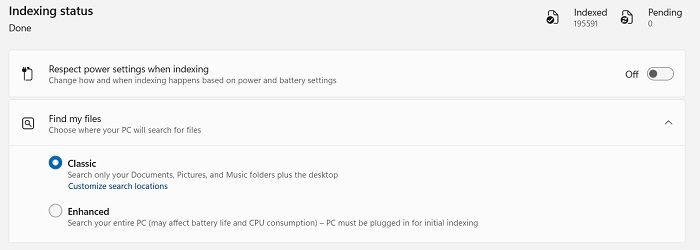
There is also a tab of Quick Searches which shows your today in history, new movies, translate, and Markets today. You can also change the Search settings and Indexing options as per your own choice.
These were some of the useful Windows 11 tips and tricks. These tips may help you increase your productivity and improve your browsing experience in the all-new Windows 11 operating system.
Bonus Tip: If your Taskbar pinned app icons overflow and there is no space, they will be moved to one convenient space.
Must read: These small cool one line, lesser-known, yet very useful one-line quick tips & tricks will help you work efficiently with your Windows computer.
You might want to take a look at the several new Windows 11 Settings that are now available; they are sure to help you get to know the OS better.
Read: Windows 11 hidden features.
What are the new features in Windows 11?
In short the new features in Windows 11 offered are:
- A sleeker, more productive design
- Snap Layout, Snap Groups brings next level Task Switching
- A better gaming experience
- Faster, personalized news for all
- A brand new Microsoft Store
- Android apps are coming to Microsoft Store
- Faster connectivity with Microsoft Teams
- Windows 11 will get just one annual Feature Update per year
- Desktop Stickers in Windows 11
This post on Windows 11 Problems, Issues with solutions, and fixes may also interest you.
Read: Windows 11 File Explorer Tips and Tricks.
Is Windows 10 or 11 better?
Windows 11 has all the features, power, and security of Windows 10. The primary difference is a redesigned desktop and the Settings menu. But apart from this, there are several other new security & productivity features under the hood. So from this point of view, we feel that Windows 11 will definitely be a worthy upgrade.
Read: How to move Taskbar to the Top on Windows 11.