Microsoft Defender Application Guard prevents potentially risky files from accessing trusted system resources. It opens untrusted documents in an isolated environment with hardware virtualization. It protects your system from malicious software in this isolated container, single standalone, and automated modes. The administrator will define some trusted websites in the automated mode, AKA Enterprise Management Mode.
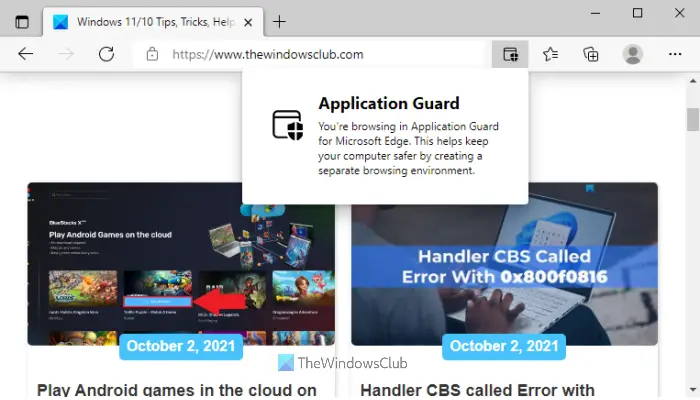
Any document or app originating from the defined domains will normally open on your computer. Meanwhile, Application Guard launches files from websites outside these defined trusted sites in the virtual environment.
Microsoft Defender Application Guard helps prevent untrusted files from accessing trusted resources, keeping your enterprise safe from new and emerging attacks. This article walks admins through setting up devices for a preview of Application Guard for Office. It provides information about system requirements and installation steps to enable Application Guard for Office on a device, says Microsoft.
How to Enable Microsoft Defender Application Guard on Windows 11
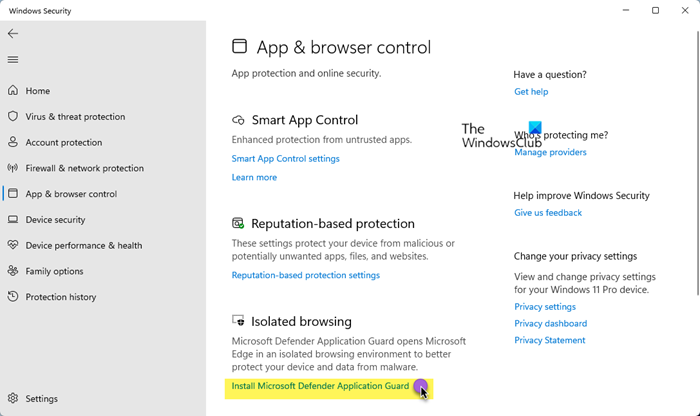
To enable and disable Microsoft Defender Application Guard on your Windows computer. We’ll explore the following:
- Enable or disable Application Guard in Windows Features.
- Enable or disable Application Guard using PowerShell.
- Install Microsoft Defender Application Guard for Edge using Command Prompt.
- Turn on Microsoft Defender Application Guard in Managed Mode group policy.
1] Turn On or Off Microsoft Defender Application Guard in Windows Features
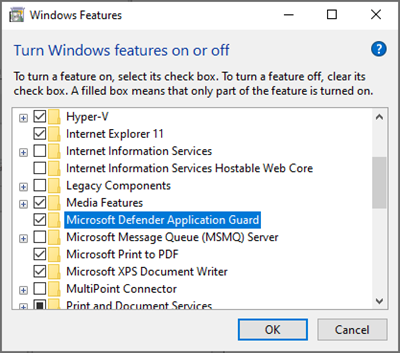
Right-click on the Start button and select Run to open the Run dialog box. Enter appwiz.cpl in the Run dialog box and click on the OK button.
Click on the Turn Windows features on or off link at the left-hand panel of the Programs and Features window.
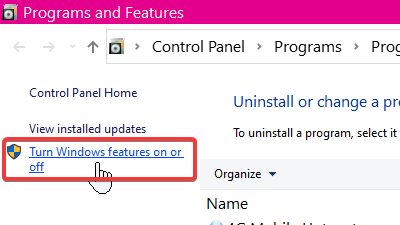
Find Microsoft Defender Application Guard from the list on the Windows Features screen and mark the checkbox next to this option to enable it. Hit the OK button.
After enabling Microsoft Defender Application Guard, you must restart your machine.
To disable Microsoft Defender Application Guard, simply uncheck the option on the Windows Features screen and restart your computer.
Read: Windows Defender Application Guard Extension for Chrome, Edge, & Firefox.
2] Enable or disable Application Guard using PowerShell
You can also enable Microsoft Defender Application Guard using PowerShell. To open PowerShell as an administrator, right-click on the Start button and select Windows PowerShell (Admin).
Copy and paste the following command in the PowerShell window to enable Windows Defender Application Guard and hit the ENTER key:
Enable-WindowsOptionalFeature -online -FeatureName Windows-Defender-ApplicationGuard
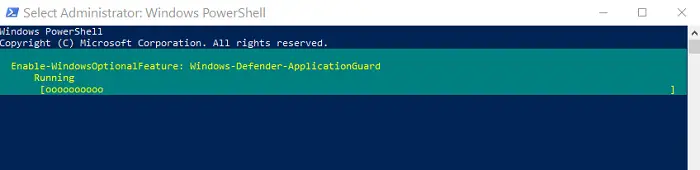
On running the above command, you’d have enabled Application Guard for Office. Restart your computer following this to finish the process.
To disable Application Guard, enter the following command:
Disable-WindowsOptionalFeature -online -FeatureName Windows-Defender-ApplicationGuard
3] Install Microsoft Defender Application Guard for Edge using Command Prompt
You need to open an elevated Command Prompt window and take the help of a built-in DISM tool to enable Application Guard for Edge browser. Here are the steps:
- Open an elevated Command Prompt window
- Run the command to install Application Guard
- Press the Y key
- Press Enter key to restart the computer and complete the operation.
Let’s check all these steps in detail.
The very first step is to open an elevated Command Prompt window. For doing this, click on the Windows 11 Search box, type cmd, right-click on Command Prompt option visible in the search results, and click on the Run as administrator option.
Now, you need to execute the following command:
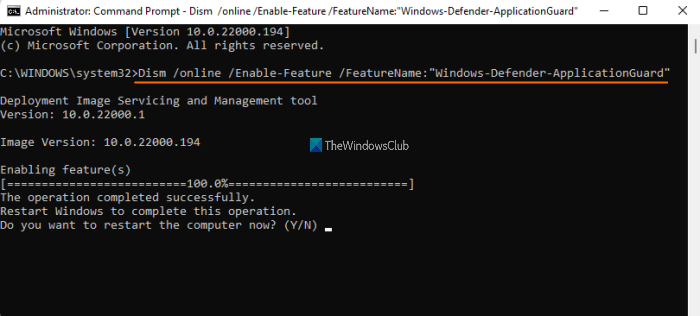
Dism /online /Enable-Feature /FeatureName:"Windows-Defender-ApplicationGuard"
As soon as you execute this command, it will start the process of enabling Application Guard. It may take a couple of minutes. After that, the Command Prompt window will prompt you to restart your computer. Press Y and then use the Enter key.
This will immediately restart your computer and start the installation process for Application Guard. Once your PC is started, the feature will be activated immediately.
4] Turn on Microsoft Defender Application Guard in Managed Mode group policy
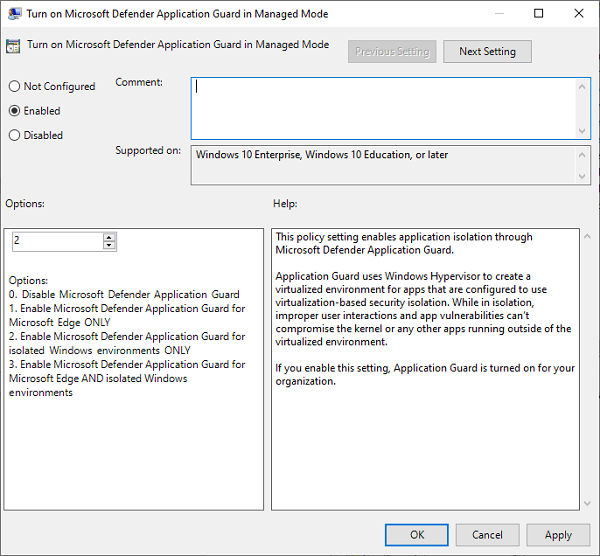
The two options above are ways to enable or disable the Application Guard for Office. After completing either of the two methods, you must turn on the feature in the Managed Mode group policy.
To do this, go to Computer Configuration > Administrative Templates > Windows Components > Microsoft Defender Application Guard.
Here, change the value under Options to 2 or 3. Click on the OK button to save your settings and close the window. Restart your computer after this.
Read: Configure Microsoft Defender Application Guard settings using GPEDIT and REGEDIT
Disable or uninstall Application Guard using CMD in Windows 11/10
If you don’t want to use the Application Guard feature anytime, you can do this easily with the following steps:
- Open an elevated Command Prompt window
- Run the command to uninstall Application Guard
- Press the Y key
- Press Enter key for restarting your PC.
Type cmd in the Search box and click on the Run as administrator option visible in the search result to open the elevated Command Prompt window.
Now execute the following command:
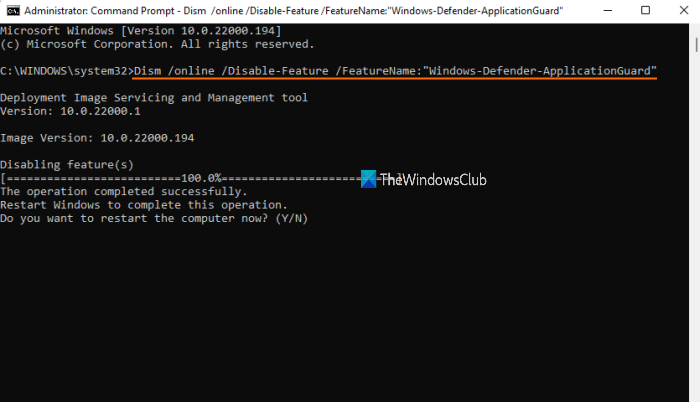
Dism /online /Disable-Feature /FeatureName:"Windows-Defender-ApplicationGuard"
Wait till the command is processed completely.
When it prompts you if you want to restart the computer, press the Y key, and then hit the enter key. Wait until the PC is restarted. This will complete the operation and remove the Microsoft Defender Application Guard.
I hope this helps.
Also read:
- How to enable Print from Application Guard for Edge
- How to enable Advanced Graphics in Application Guard for Edge
- How to enable Advanced Graphics in Application Guard for Edge
- Enable Camera and Microphone in Microsoft Defender Application Guard for Edge.
What is Microsoft Defender Application Guard?
Microsoft Defender Application Guard has been created to target 3 types of enterprise systems:
- Enterprise desktops
- Enterprise mobile laptops
- Bring your own device (BYOD) mobile laptops.
This feature uses virtualization technology to open links clicked while browsing the Internet or checking email in a sandboxed environment (an isolated environment to test or analyze software in a protected environment) to keep malicious scripts out of the user’s network and devices.
Says Microsoft,
Application Guard helps to isolate enterprise-defined untrusted sites, protecting your company while your employees browse the Internet. As an enterprise administrator, you define what is among trusted web sites, cloud resources, and internal networks. Everything not on your list is considered untrusted. If an employee goes to an untrusted site through either Microsoft Edge or Internet Explorer, Microsoft Edge opens the site in an isolated Hyper-V-enabled container, which is separate from the host operating system. This container isolation means that if the untrusted site turns out to be malicious, the host PC is protected, and the attacker can’t get to your enterprise data.
Considering the latest developments in which many business establishments worldwide have come under direct security threat, this new layer of defense-in-depth protection offered by Microsoft Defender Application Guard is welcome.
It is a fact that over 90% of attacks are initiated via a hyperlink designed specifically to:
- Steal credentials
- Install malware
- Exploit vulnerabilities.
So, initially, a corrupt email, often disguised as a legitimate authority in the company, may request the employee click a link to read a supposedly important document.
The link is specially crafted to install malware on the user’s machine. Once a connection is established on that computer, the attackers can easily steal credentials and look for vulnerabilities in other computers on the same network.
With virtualization technology supported in Microsoft Defender Application Guard, potential threats are identified, segregated from the network and system, and removed completely when the container is closed.
Secondly, when an employee browses to a site not trusted by the network administrator, the Application Guard immediately removes the potential threat. As shown in the image below outlined in red, Application Guard creates a new instance of Windows at the hardware layer with a completely different copy of the kernel. The underlying hardware (Windows Defender Application Guard) enforces that this separate copy of Windows has no access to the user’s normal operating environment, which includes access to memory, local storage, other installed applications, and corporate network endpoints.
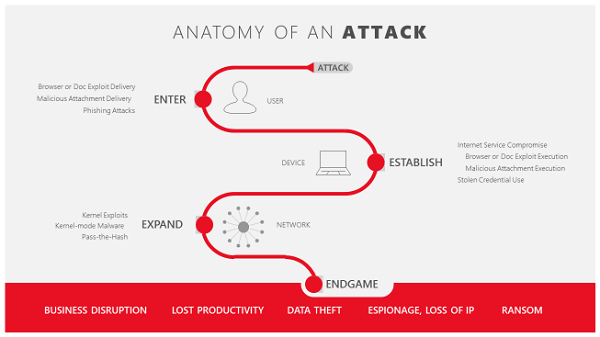
In-depth defense for Enterprise
Microsoft Defender Application Guard can offer its customers a trouble-free browsing experience by protecting enterprise systems from advanced attacks that seek entry to the network and devices via the Internet. It even has a definite plan of action when malicious code manages to enter the network. The ingenious tool silently coordinates with Microsoft Edge to open that site in a temporary and isolated copy of Windows. In this case, even if the attacker’s code successfully exploits the browser, the attacker finds their code running in a clean environment with no interesting data, no access to any user credentials, and no access to other endpoints on the corporate network. The attack thus loses its prominence and invariably gets disrupted.
Soon after the browsing session is complete, the temporary container is thrown away alongside the malware. All this happens quickly and the user does not even get a hint of an attack taking place. After deletion, a fresh new container is created for future browsing sessions.
Web developers and Application Guard
The news that brings much joy for web developers is that they do not need to do anything different or new with their site code – Microsoft Edge renders sites in Application Guard fundamentally the same way it does in the host version of Windows. There is no essential requirement to detect malicious code when Microsoft Edge is running in this mode, nor is there any need to account for behavior differences. Since this temporary container is destroyed when the user is done, cookies or local storage are not allowed when the user is finished.
In addition, Microsoft made other security announcements like Microsoft Defender Application Guard and Office 365 ATP, which now have the capacity to mutually share intelligence and assist IT professionals in investigating and responding to security threats across both Windows and Office 365 in a timely manner.
How to Install Microsoft Defender Application Guard for Microsoft Edge?
Execute the following command to Install Microsoft Defender Application Guard for Microsoft Edge:
Dism /online /Enable-Feature /FeatureName:"Windows-Defender-ApplicationGuard"
As soon as you execute this command, it will start enabling Application Guard.