In this digital age of technology, technology helps us connect and be more productive. But have you ever wondered how secure they are? Specter and Meltdown vulnerabilities, which exploit critical vulnerabilities in modern processors, have just been discovered. These hardware bugs allow programs to steal data being processed on the computer.
What is Meltdown vulnerability?

Meltdown breaks the most fundamental isolation between user applications and the operating system. This attack allows a program to access the memory, and thus also the secrets, of other programs and the operating system.
This vulnerability would allow malicious attacks to occur when a hacker could break the differentiating factor between the applications run by the user and the computer’s Core Memory.
Severity:
We would like to call Meltdown one of the most dangerous vulnerabilities ever found, at least for a CPU. Daniel Gruss is one of the researchers at Graz University of Technology and is one of the people responsible for discovering this flaw. In a statement, he said:
Meltdown is probably one of the worst CPU bugs ever found!
He also talked about the urgency of this situation and how important it is to fix this flaw on such quick notice as it leaves serious vulnerability to users all around the globe. This leaves millions of devices vulnerable to serious attacks. This is so important to be fixed because anything that runs as an application can steal your data. This includes any application programs or Javascript script running on a web page in any browser. This makes Meltdown dangerous for us and easy for hackers.
What is Spectre vulnerability?
Spectre breaks the isolation between different applications. It allows an attacker to trick error-free programs, which follow best practices, into leaking their secrets. In fact, the safety checks of said best practices actually increase the attack surface and may make applications more susceptible to Spectre
Spectre is slightly different from Meltdown. This is so because it can allow hackers to fool the applications (even the stable versions of the respective application) running on a machine to give up secret information from the Kernal module of the operating system to the hacker with the consent or knowledge of the user.
Severity:
Even though it is harder for hackers to take advantage of, you should always be careful because you are vulnerable. Also, it is worth noting that it is harder to fix and can lead to a bigger issue in the long-term plans.
Are you affected by Spectre or Meltdown vulnerabilities?
Desktop, Laptop, and Cloud computers may be affected by Meltdown. Every Intel processor that implements out-of-order execution is potentially affected, effectively every processor since 1995 (except Intel Itanium and Intel Atom before 2013). At the moment, it is unclear whether ARM and AMD processors are also affected by Meltdown. As far as Spectre is concerned, almost every system is affected by it- Desktops, Laptops, Cloud Servers, and Smartphones.
If you are running any modern processors, whether Intel makes them, AMD or ARM, or what device you are using, you are vulnerable to Spectre. On the other hand, if you run Intel chips manufactured since 1995, you are vulnerable. But there is an exception for Itanium and Atom chips made before 2013.
Who has been attacked yet?
As per the information from UK’s National Cyber Security Centre, the is no current trace of Meltdown or Spectre affecting any machines around the globe, but it is also worth noting that these attacks are so sensitive that they are challenging t to be detected.
Experts have said they expect hackers to quickly develop programs to attack users based on the vulnerability as it is public now. Chief Executive of Cybersecurity Consulting firm Trail of Bits, Dan Guido, said:
Exploits for these bugs will be added to hackers’ standard toolkits.
Here is how you can stay safe:
You need to keep all your device updated with the newest fixes available. Enabling Strict Site Isolation in Chrome and preventing JavaScript from loading are the other precautions you could take.
However, US-CERT has said – “Replace CPU hardware. CPU architecture design choices primarily cause the underlying vulnerability. Fully removing the vulnerability requires replacing vulnerable CPU hardware.”
We know that fixes for Linux and Windows Operating Systems are already available. Chromebooks are already safe if they run Chrome OS 63, which was released in mid-December to the public. If your Android phone runs the latest security patch, it is already protected. For users having Android phones from other OEMs like OnePlus, Samsung, or any other OEM, you have to wait for an update from them about the same. Most of the popular browsers & software developers have released updates – and you need to ensure that you have updated your software to the latest version.
Microsoft has released a PowerShell cmdlet that lets you determine if your Windows computer is affected by Meltdown and Spectre CPU Vulnerabilities and suggests ways to protect your system.
A list of continually updated compatible antivirus & security software is available here.
Do these fixes affect the performance of my machine?
Well, it is said that the fixes for Spectre won’t immediately affect the machine’s performance, but the fixes for Meltdown will significantly affect the performance.
If you wish to dig more into these vulnerabilities, you can refer to this official documentation about the same here.
Related read: Intel processors have design flaws, resulting in ‘Kernal Memory Leaking’.
Find out if your Windows is affected by Meltdown and Spectre CPU Vulnerabilities.
Most of you must have read about the Spectre and Meltdown CPU vulnerabilities and wondered if there is anything you need to do to protect yourself against these CPU vulnerabilities. Microsoft has released a PowerShell cmdlet that lets you determine if your Windows computer is affected by Meltdown and Spectre CPU Vulnerabilities and suggests ways to protect your system.
Find out if your Windows is affected by Meltdown & Spectre
Run PowerShell as administrator and execute the following commands one after the other:
PS> # Save the current execution policy so it can be reset PS> $SaveExecutionPolicy = Get-ExecutionPolicy PS> Set-ExecutionPolicy RemoteSigned -Scope Currentuser PS> CD C:\ADV180002\SpeculationControl PS> Import-Module .\SpeculationControl.psd1 PS> Get-SpeculationControlSettings PS> # Reset the execution policy to the original state PS> Set-ExecutionPolicy $SaveExecutionPolicy -Scope Currentuser
This will install, activate an additional module and enable protection.
Check the output and see if all the elements show a value of True. That shows that your Windows is protected. If it shows False, your system is vulnerable, and you need to fix those issues.
You can, later on, restore the default ExecutionPolicy setting by running executing this Set-ExecutionPolicy Default command.
For more information, you may visit Microsoft.
Protect Windows against Meltdown & Spectre
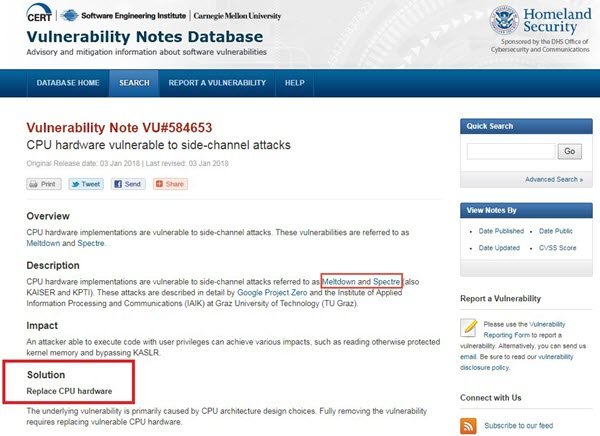
US-CERT has said – “Replace CPU hardware. CPU architecture design choices primarily cause the underlying vulnerability. Fully removing the vulnerability requires replacing vulnerable CPU hardware.”
However, there are some basic precautions you can take to protect your Windows against Meltdown and Spectre CPU Vulnerabilities:
- Ensure that your device firmware and the operating system are fully patched with the latest updates.
- Ensure that all your installed software, especially web browsers, are updated to their latest versions. You may use a Software Update Checker.
- Enable Strict Site Isolation in Chrome and prevent JavaScript from loading in your browser.
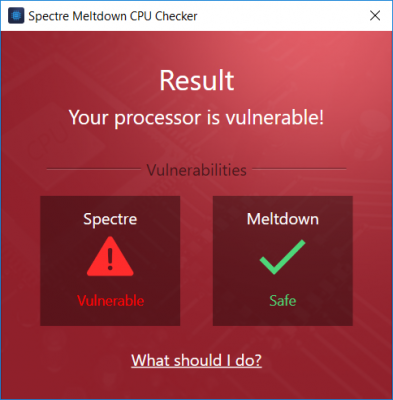
Ashampoo Spectre Meltdown CPU Checker will easily check if your Windows computer is vulnerable.
The tool is simple and easy to use. You do not need to run any script or cmdlet. You can use the simple GUI to check your computer for vulnerabilities. Once downloaded, Ashampoo Spectre Meltdown CPU Checker will scan your CPU. The scan might take a little while, and towards the end, it will show you the result. The program displays whether your computer is affected by any Spectre or Meltdown vulnerabilities.
Stay safe!