Though security concerns with systems are nowhere new, the mess caused by the Wannacrypt ransomware has prompted immediate action among netizens. The Ransomware targets the vulnerabilities of the SMB service of the Windows operating system to propagate.
SMB or Server Message Block is a network file sharing protocol meant for sharing files, printers, etc, between computers. There are three versions – Server Message Block (SMB) version 1 (SMBv1), SMB version 2 (SMBv2), and SMB version 3 (SMBv3). Microsoft recommends that you disable SMB1 for security reasons – and it is now more important to do so in view of the WannaCrypt or NotPetya ransomware epidemic.
Should you disable SMB1?
Yes, SMBv1 should be disabled on all systems without a business justification for its use. Disabling SMBv1 enhances security by reducing vulnerability to ransomware and other malware attacks.
Disable SMB1 on Windows 11/10
To defend yourself against WannaCrypt ransomware it is imperative that you disable SMB1 as well as install the patches released by Microsoft. Let us take a look at some of the ways to disable SMB1 on Windows 11/10/8/7.
Turn Off SMB1 via Control Panel
Open Control Panel > Programs & Features > Turn Windows features on or off.
In the list of options, one option would be SMB 1.0/CIFS File Sharing Support. Uncheck the checkbox associated with it and press OK.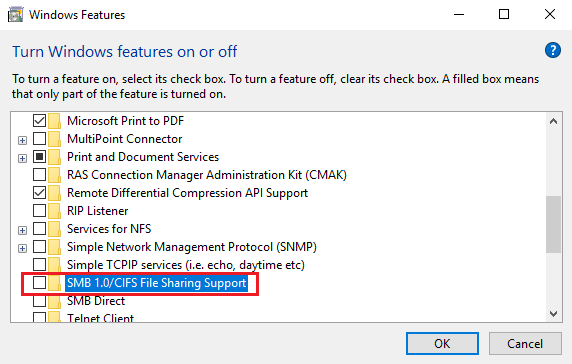
Restart your computer.
Related: How to enable or disable SMBv2 in Windows.
Disable SMBv1 using Powershell
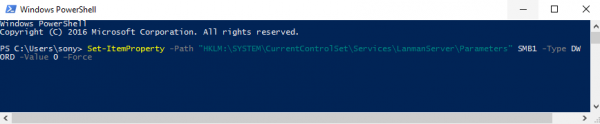
Open a PowerShell window in the administrator mode, type the following command and hit Enter to disable SMB1:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB1 -Type DWORD -Value 0 –Force
If for some reason, you need to temporarily disable SMB version 2 & version 3 use this command:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB2 -Type DWORD -Value 0 –Force
It is recommended to disable SMB version 1 since it is outdated and uses technology that is almost 30 years old.
Says Microsoft, when you use SMB1, you lose key protections offered by later SMB protocol versions like:
- Pre-authentication Integrity (SMB 3.1.1+) – Protects against security downgrade attacks.
- Insecure guest auth blocking (SMB 3.0+ on Windows 10+) – Protects against MiTM attacks.
- Secure Dialect Negotiation (SMB 3.0, 3.02) – Protects against security downgrade attacks.
- Better message signing (SMB 2.02+) – HMAC SHA-256 replaces MD5 as the hashing algorithm in SMB 2.02, SMB 2.1 and AES-CMAC replaces that in SMB 3.0+. Signing performance increases in SMB2 and 3.
- Encryption (SMB 3.0+) – Prevents inspection of data on the wire, MiTM attacks. In SMB 3.1.1 encryption performance is even better than signing.
In case you wish to enable them later (not recommended for SMB1), the commands would be as follows:
For enabling SMB1:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB1 -Type DWORD -Value 1 -Force
For enabling SMB2 & SMB3:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB2 -Type DWORD -Value 1 –Force
Disable SMB1 using Windows registry
You can also tweak the Windows Registry to disable SMB1.
Run regedit and navigate to the following registry key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
On the right side, the DWORD SMB1 should not be present or should have a value of 0.
The values for enabling and disabling it are as follows:
- 0 = Disabled
- 1 = Enabled
For more options and ways to disable SMB protocols on the SMB server and the SMB client visit Microsoft.
Is SMB1 disabled by default?
Yes, SMB1 is disabled by default because it is considered deprecated and insecure. Users can re-enable it if necessary, but it is generally recommended to use more secure versions of SMB to protect your network.
How do I enable SMB1 on Windows?
To enable SMB1 on Windows, go to Control Panel > Programs > Turn Windows features on or off. Check the “SMB 1.0/CIFS File Sharing Support” box and click OK. Restart your computer for the changes to take effect. This allows Windows to support SMBv1 for accessing network devices.
Now read: How to Disable NTLM Authentication in Windows Domain.