We have been covering several NirSoft utilities recently. Here is another interesting packet sniffer utility called WebSiteSniffer. A packet sniffer is a hardware piece or a computer program that intercepts traffic passing over a digital network. It can be useful in many ways like detecting network intrusion attempts, analyzing network problems, gathering and reporting network statistics, etc.
Gather Network Statistics with WebSiteSniffer
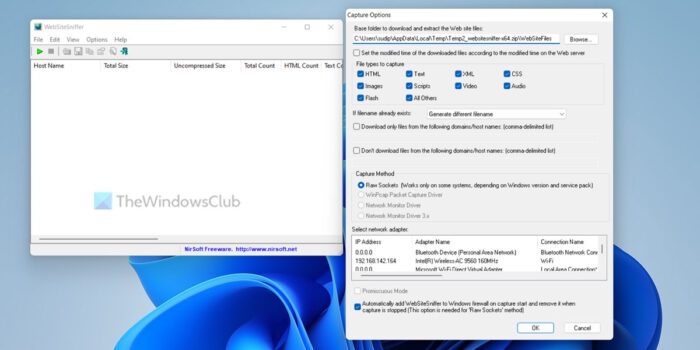
WebSiteSniffer is one such small packet sniffer application that captures all website files (HTML files, Flash, Video, images, scripts, and other content files) automatically while browsing the Internet and stores them under a preferred folder.
The freeware is capable of working with any web browser, regardless of the browser cache settings.
It has the following requirements,
- WinPcap Capture Driver. It is an open-source driver that permits you to capture network packets on Windows (any version:
- Microsoft Network Monitor (3.x) new version
- Microsoft Network Monitor Driver version (2.x) only for Windows 2000/XP/2003
To download and install WebSiteSniffer simply click on the link provided at the end of the article. Scroll the page to locate the ‘Feedback’ column and click on ‘Download WebSiteSniffer’ option to begin downloading.
Double-Click on the downloaded icon and click on ‘Extract’ to unzip and extract the contents of the zip-file to a preferred folder. You will soon find your file extracted. Simply run the executable file – WebSiteSniffer.exe.
After the application has been used, the main window of the program will display the general statistics of some downloaded files along with their host name, total size of the files (compressed/uncompressed) and the total number of files for every file type.
Though useful in gathering and reporting network statistics, the freeware application has some shortcomings and limitations. It requires enabling of the ‘private browsing’ option for the capture of some files and is inefficient to capture files from secured websites. Download WebSiteSniffer from here.
How do I capture network packets in Windows?
As it is not possible to capture network packet statistics in Windows using in-built apps, you need to take the help of a third-party program called WebSiteSniffer. This freeware allows users to gather all the details about your network statistics. Whether you use Windows 11, Windows 10, Windows 8.1/8, or Windows 7, you can use this free program on your computer without any issue.
Can you use tcpdump on Windows 11/10?
Yes, you can use tcpdump on Windows 11/10 PC. This functionality is compatible with Windows XP to Windows 11. On the other hand, you can use the same on Windows server 2016, Windows Server 2019, and Windows PE. However, you must use an elevated form of the Command Prompt or the Command Prompt instance in Windows Terminal.
Hope it helped.
Leave a Reply