Using a vulnerability in the SSL 3.0, attackers can inject malicious code into your computer and compromise it. They can also compromise web hosting servers using the same SSL 3.0. Most browsers still support SSL3, as most web servers still use SSL 3.0 for communication such as login, filling up forms of any kind, etc.
Poodle Security Attack

Secure Sockets Layer or SSL is a cryptographic protocol designed to provide communication security over the Internet. It is now superseded by Transport Layer Security or TLS.
The Poodle attack allows a web criminal to intercept data that is being sent over the SSL3 connection. Not only can he or she intercept the data, but the web criminal can also inject their own data into the connection, making the website believe that it came from the browser. Likewise, it makes the browser believe that malicious data comes from the web server.
POODLE is short for Padding Oracle On Downgraded Legacy Encryption. It is a protocol flaw and not related to implementation. It means that irrespective of how SSL3 is implemented by browsers or hosts, the flaw will be there for attackers to exploit. The only method to save yourself from being hacked is to disable SSL3.0 in your browsers and at your web hosting servers.
You can test your browsers’ vulnerability by visiting this website using the browser you wish to check: ssllabs.com.
Disable SSL 3.0
To protect yourself against Poodle security attacks, you might want to turn off or lock down SSL 3.0 in your web browser.
Internet Explorer: Open the Internet Options dialog from Control Panel and go to the advanced tab. Check for Use SSL 3.0 and uncheck it.
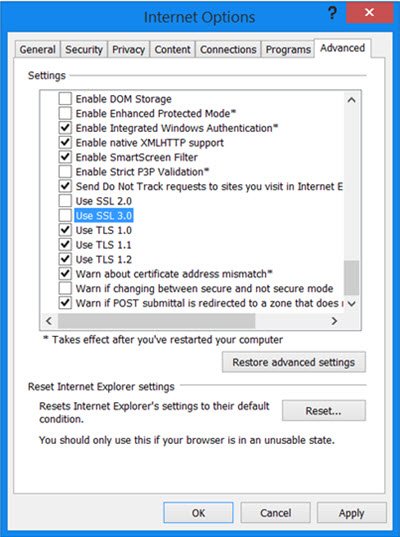
Microsoft has released a Fix-It that lets users disable SSL 3.0 in Internet Explorer. Microsoft has also announced that SSL 3.0 will be disabled in the default configuration of Internet Explorer and across Microsoft online services over the coming months, and recommends that customers migrate clients and services to more secure security protocols, such as TLS 1.0, TLS 1.1 or TLS 1.2.
Firefox: To get to the option to disable SSL3, type “about:config” in the address bar. Search for security.tls.version.min in the results or use the search bar to look for it. Double-click on the row and change the value from 0 to 1. This will force Firefox to use only TLS1.0 and above thereby disabling SSL3.0.
Firefox has already said it will disable SSL 3.0 in their next release, just as they disabled Java 6 when the latter was found to be highly vulnerable.
Google Chrome: It is not visible in the Settings. One has to add a parameter to the Chrome shortcut so that it disables SSL3 and forces TLS only. Right-click on its shortcut and select Properties. In the field labeled Target, append –ssl-version-min=tls1. So your path should appear as:
"C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --ssl-version-min=tls1
Even Google has said that, in the coming months, it hopes to remove support for SSL 3.0 completely from all its client product.
Site owners or Hosts: As a web site owner or a web host, you should consider disabling SSL 3 on your servers, as soon as possible
For complete details of the POODLE attack and SSL 3.0 vulnerability, please visit oracle.com.
Your procedure for setting in Google Chrome is INCORRECT and does NOT work !
This is correct procedure: “My understanding is that the user can configure SSL/TLS settings for Chrome browser from [Settings] -> [Change Proxy Settings] -> [Advanced].”
There are two dashes “-” before the ssl. But they are appearing merged in the text above. So I have added a new line which gives the full path after it is appended
Thanks for this reminder! In return, here are three reminders about Firefox configurations which some have an interest in: first, re “about:config”, browser.display.use_document_fonts will always revert to a value of “1” every time the browser is closed/re-opened (those wishing to have Firefox blab about fewer fonts always have to reset the value to “0” as it doesn’t persist); second, browsersession.max_entries will always revert to a value of “50” every time FF is closed/re-opened (those wanting to have FF blab less about number of pages in tab history will have to reset the value to “2” every time they open FF…setting doesn’t persist); and finally, dom.storage.enabled has to be reset to “false” every time as this change too never persists, for those who don’t want dom storage. Thanks again, cheers!
That is a very cute poodle!
real activation, to get what you want by search @@@windows 8.1 key sale@@@ from bing.