Email Spoofing is a type of phishing. We all know about Phishing, how it works and how to avoid phishing. Basically, they are cybercriminals who tend to set up different types of baits with the intention to extract valuable information from you. In most cases, they want your information about the financial institutions where you may have accounts – banking institutions, card companies, PayPal, etc. They use plenty of techniques to make it look like genuine emails and messages.
What is Email Spoofing
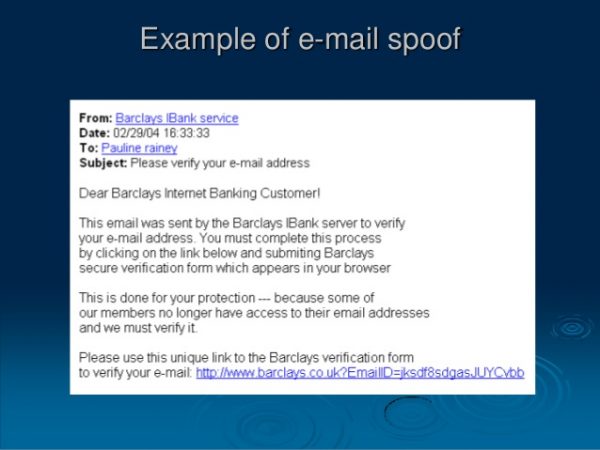
As the name suggests, cybercriminals spoof emails in a way that it appears to be originating from someone you trust. What is email spoofing? One can define email snooping as the method where cybercriminals ‘use’ others’ valid email IDs to send you phishing emails and messages.
For example, you might receive an email from some financial institution like PayPal or your bank. There won’t be anything suspicious in the email as the email ID is related to PayPal. The only difference you might find in spoofed emails is that they are asking you for your personal and/or financial information. It might just say, update your information and ask you to click on the link in the email.
No matter what, never ever click links even in genuine emails if they are asking you to update your information. Type the URL manually and then do the needful. You never know which email is just a phishing attempt.
How does Email Spoofing work
In case you have seen the email account configuration in your email clients, you will see that the outgoing server always contains SMTP (Simple Mail Transfer Protocol). Every user and mail provider on the Internet uses SMTP to send mails. The protocol is, however, exploitable. It is the reason you can’t kill all spam at the entry. The protocol was last updated in the year 2008 (as of writing this article) and yet does not incorporate filters to differentiate original email headers from tampered headers.
Not to confuse you here, but when you send an email using webmail and email clients, the webmail or clients attach a header to the email so that the recipient webmail and clients know the path it traveled to reach the recipient. These headers can easily be exploited and edited manually.
In case you are wondering how anyone can send emails using your email ID, it takes just a little alteration to these headers to make it show that the email originated from your email ID. Now, if you receive an email from your own email ID, you will get curious or worry if the ID is compromised. While it is better to keep the password changing, in most cases, it may be just email spoofing.
How to protect from email spoofing
Most of the rules to protect yourself from email spoofing are the same as in the case of phishing:
- If the email doesn’t make sense, delete it
- If the email comes from your financial institution but asks for your password or some other information, call up the financial institution and ask if they really sent you the email. Chances are high that they have not.
- No matter what, never click links in the email to open your bank websites; always type them in the browser address bar manually
While the above are common, the best method to protect from email spoofing is to use digital signatures. There are many companies that provide email digital signatures, including some that provide it for free. If you send a digitally signed email, the email client at the receivers’ end will analyze the header to search for tampering. If it finds anything fishy, it will notify you when you try to open the email.
In any case, if you get a spoofed email, notify the relevant institution. While notifying the institution, you may also include a CC to “cert@cert.org” so that the cybercrime cells can also take a look at it.
A safe path to follow: If you receive an email purporting to be from your Bank, Credit Card provider, PayPal or financial institution asking you to click on a link and change something, ignore it.
Some of you might want to read about Business Email Compromise here.
Leave a Reply