The PIN sign-in in Windows 10/8 helps us to log in to the system using an easy-to-remember 4 digit number. PIN sign-in is a bit handy as compared to Password and Picture password options. However, one disadvantage of PIN sign-in, is that it doesn’t work when your system is in Safe Mode.
PIN Sign-in is disabled when the system is joined to Domain
If you are running a Windows 10 system that is joined to a domain, you may not able to create or log on using PIN.
When you visit the Settings > Accounts > Sign-in options section to create the PIN, you may find that the option to create is grayed out i.e. disabled.
There is no error or message displayed for the option disabled there. If your PIN Sign-in is disabled & grayed out when Windows is joined to a domain, turn on & enable PIN sign-in for Domain users by following this tutorial.
Enable & Turn on PIN sign-in for Domain users
You can turn on & enable PIN sign-in in Windows 11/10 using the Group Policy if your PIN Sign-in is disabled when the system is joined to a Domain. This method is only In Windows 11/10/8 Pro & Enterprise Editions.
1. Press Windows Key + R combination, type put gpedit.msc in Run dialog box and hit Enter to open the Local Group Policy Editor.
2. In the left pane of Local Group Policy Editor, navigate here:
Computer Configuration -> Administrative Templates -> System -> Logon -> Turn on pin sign-in
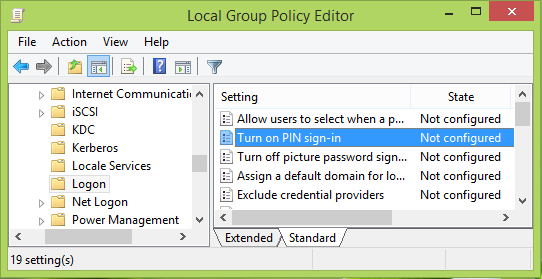
3. In the right pane of the above-shown window, look for the setting named Turn on PIN sign-in which must be Not Configured by default. Double click on the same setting to get this:
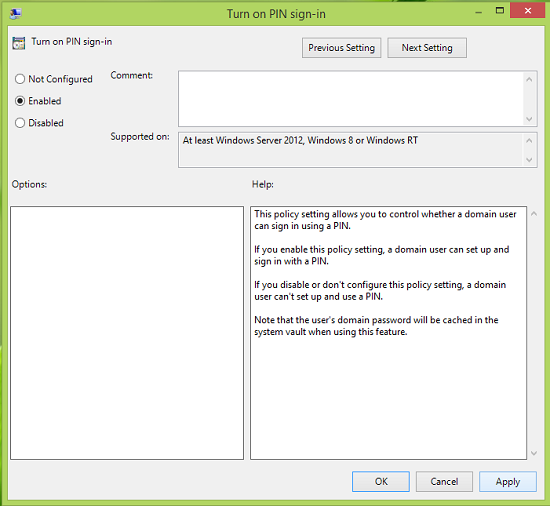
4. Finally, in the above-shown window, click Enabled and then click Apply followed by OK.
You can now close the Local Group Policy Editor window and reboot the machine. After restarting the system, you should be able to use create and use PIN sign-in.
Hope this helps – Good luck!